Products You May Like
Akamai’s ransomware report launched at Black Hat 2023 revealed that exploitation of zero-day and one-day vulnerabilities has led to a 143% improve in whole ransomware victims with knowledge exfiltration of recordsdata on the finish of the kill chain, now the first supply of extortion.
Soar to:
LockBit within the lead, CL0P in 2nd
The report, Ransomware on the Move, checked out how exploitation strategies are evolving — together with attackers’ sharpened deal with zero-day vulnerabilities. It confirmed how victims of a number of ransomware assaults have been greater than six occasions extra prone to expertise the second assault inside three months of the primary assault.
The authors from Akamai’s Safety Intelligence Group reviewed knowledge from the fourth quarter of 2021 to the second quarter of 2023. The authors reported that LockBit ensnared round 39% of all sufferer organizations tracked by Akamai, which stated LockBit’s sufferer depend is thrice that of its nearest competitor, the CL0P group. Quantity three in quantity of victims, ALPHV, aka Black Cat, targeted its efforts on creating and exploiting zero-day factors of entry (Determine A).
Determine A
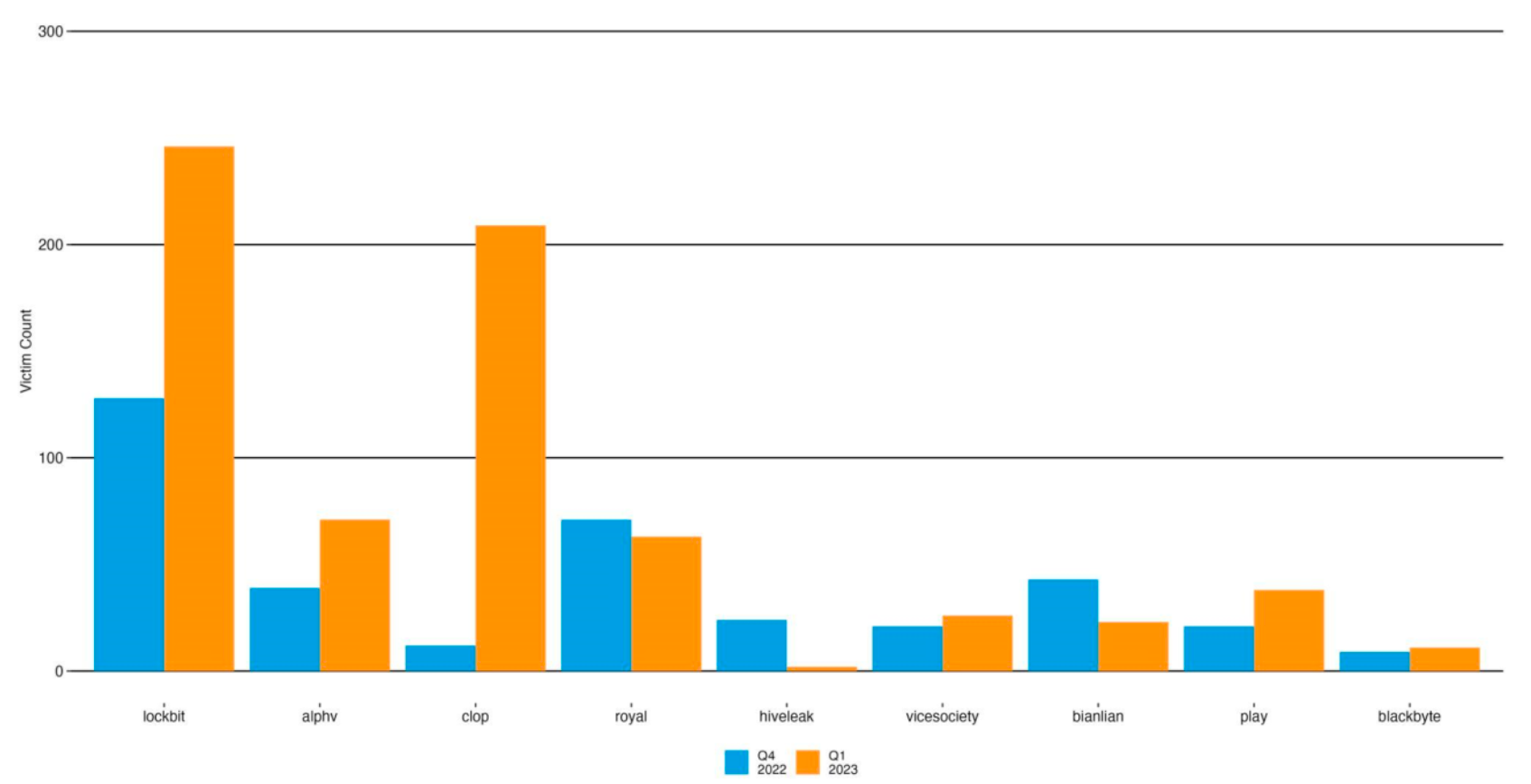
- High ransomware teams by sufferer depend. Picture: Akamai
Anthony Lauro, director of safety know-how and technique at Akamai, defined that LockBit appears to be like for top worth targets with zero day vulnerabilities that firms can’t repair shortly. They have a tendency to focus on and retarget these organizations and the sectors — like manufacturing and know-how for instance — the place safety operations are lagging, usually. Additionally, he defined, malware writers can select instruments and providers from a rising darkish ecosystem.
Two clear tendencies present how threats are evolving
The report spotlighted two tendencies that talk to how giant teams — with attain and breadth of merchandise together with RaaS — have a steady progress and smaller teams deal with alternatives as they come up:
- The primary is exemplified by LockBit, characterised by a gentle depend of fifty victims per thirty days, and exercise appears tied to its variety of associates and its assets.
- The second, typified by teams like CL0P, function spikes in exercise from abusing essential zero-day vulnerabilities as they seem, and extremely focused safety flaws.
“Malware writers can now split off operations, which is a change,” stated Lauro. “It used to be that the attackers were a single entity or group that would be responsible for malware payload delivery, exploitation and follow up.” He added that, due to the open nature of the malware market, teams like LockBit and Cl0P have been in a position to co-opt others to carry out varied duties within the provide kill chain.
ALPHV: Rust by no means sleeps
Lauro stated throughout the ways discovered extra usually within the second development group, “Are the tried and true methodologies, like Windows system vulnerabilities that are not necessarily high severity because these systems aren’t usually available to outside queries. Attackers can still access them. So, there are two major trends: spreading the victim base across easy targets and tactics and ones leveraging CVE and zero days looking at big players as targets.”
ALPHV, for instance, second on Akamai’s checklist of attackers when it comes to sufferer quantity, makes use of the Rust programming language to contaminate each Home windows and Linux techniques. Akamai stated the group exploited vulnerabilities in Microsoft Alternate server to infiltrate targets.
In keeping with Akamai, the group spoofed a sufferer’s web site final yr (utilizing a typosquatted area). The brand new extortion approach included publishing the stolen recordsdata and leaking them on their web site so as to tighten the thumbscrews on victims and encourage ransom cost.
Mid-sized organizations are the ‘Goldilocks zone’ for risk actors
In Akamai’s research, 65% of focused organizations had reported income of as much as $50 million {dollars}, whereas these price $500 million {dollars} and up constituted 12% of whole victims, in response to Akamai. Additionally they reported that the ransomware knowledge used was collected from the leak websites of roughly 90 completely different ransomware teams.
Let’s name it ‘Cyberfracking’
When you had invested in a pure fuel mining operation, you may “accidentally on purpose” attain out sideways to belongings beneath different peoples’ lawns when you’d tapped out the goal. LockBit attackers are likewise reaching out to sufferer’s clients, informing them in regards to the incident and using triple extortion ways with the inclusion of Distributed Denial-of-Service assaults.
Lauro stated completely different levels of exploitation and supply and execution are the primary two steps. Protection is based on edge protection components like visibility, however the remainder of it’s after the very fact, transferring laterally and tricking techniques, or making requests that appear like a “friendly” — all contained in the community.
SEE: Have a look at your APIs! Akamai says observability tools sorely lacking (TechRepublic)
“Once you’re inside most organizations are wide open, because as then, an attacker I don’t have to download special toolkits; I can use installed tools. So there is a lack of good localized network security. We are finding more and more environments in bad shape in terms of internal visibility and over time,” he stated.
CL0P for a day … a zero day
CL0P, which is quantity three when it comes to its quantity of victims over the course of Akamai’s statement interval, tends to abuse zero-day vulnerabilities in managed file switch platforms. Akamai stated the group exploited a legacy file switch protocol that has been formally old-fashioned since 2021, in addition to a zero-day CVE in MOVEit Switch to steal knowledge from a number of organizations.
“It is worth noting how CL0P has a relatively low victim count until its activity spikes whenever a new zero-day vulnerability is exploited as part of its operation,” stated the Akamai report authors. “And unlike LockBit, which has a semblance of consistency or pattern, CL0P’s attacks are seemingly tied to the next big zero-day vulnerability, which is hard to predict (Figure B).”
Determine B
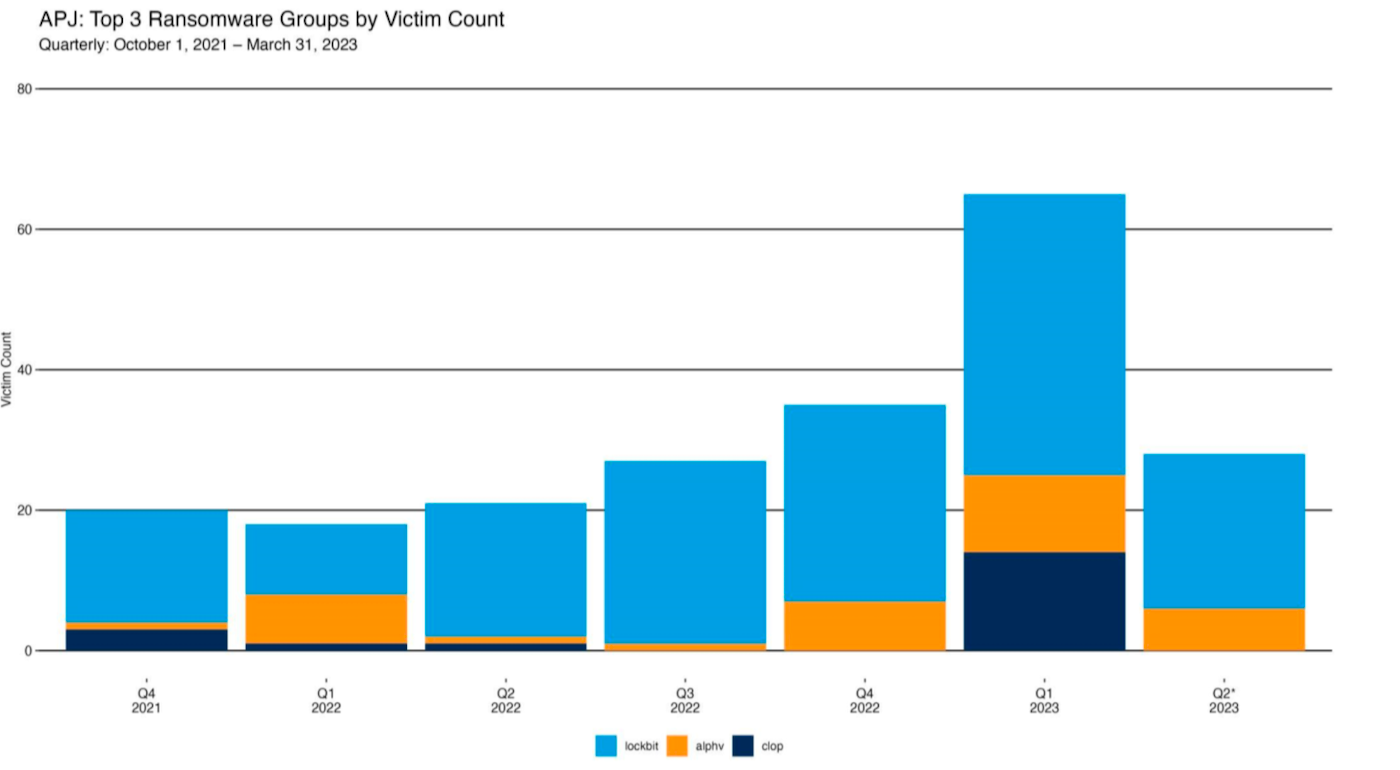
- A comparability of quarterly sufferer counts among the many prime three ransomware teams: LockBit, ALPHV and CL0P. Picture: Akamai
LockBit: a turnkey resolution
Akamai famous that LockBit, whose web site appears to be like like a reliable net concern, is touting new instruments and even a bug bounty program in its newest 3.0 model. Similar to white hats, the group is inviting safety researchers and hackers to submit bug stories of their software program for rewards ranging as much as $1 million.
Akamai famous that whereas the bug bounty program is principally defensive, “It’s unclear if this will also be used to source vulnerabilities and new avenues for LockBit to exploit victims.” (Determine C).
Determine C
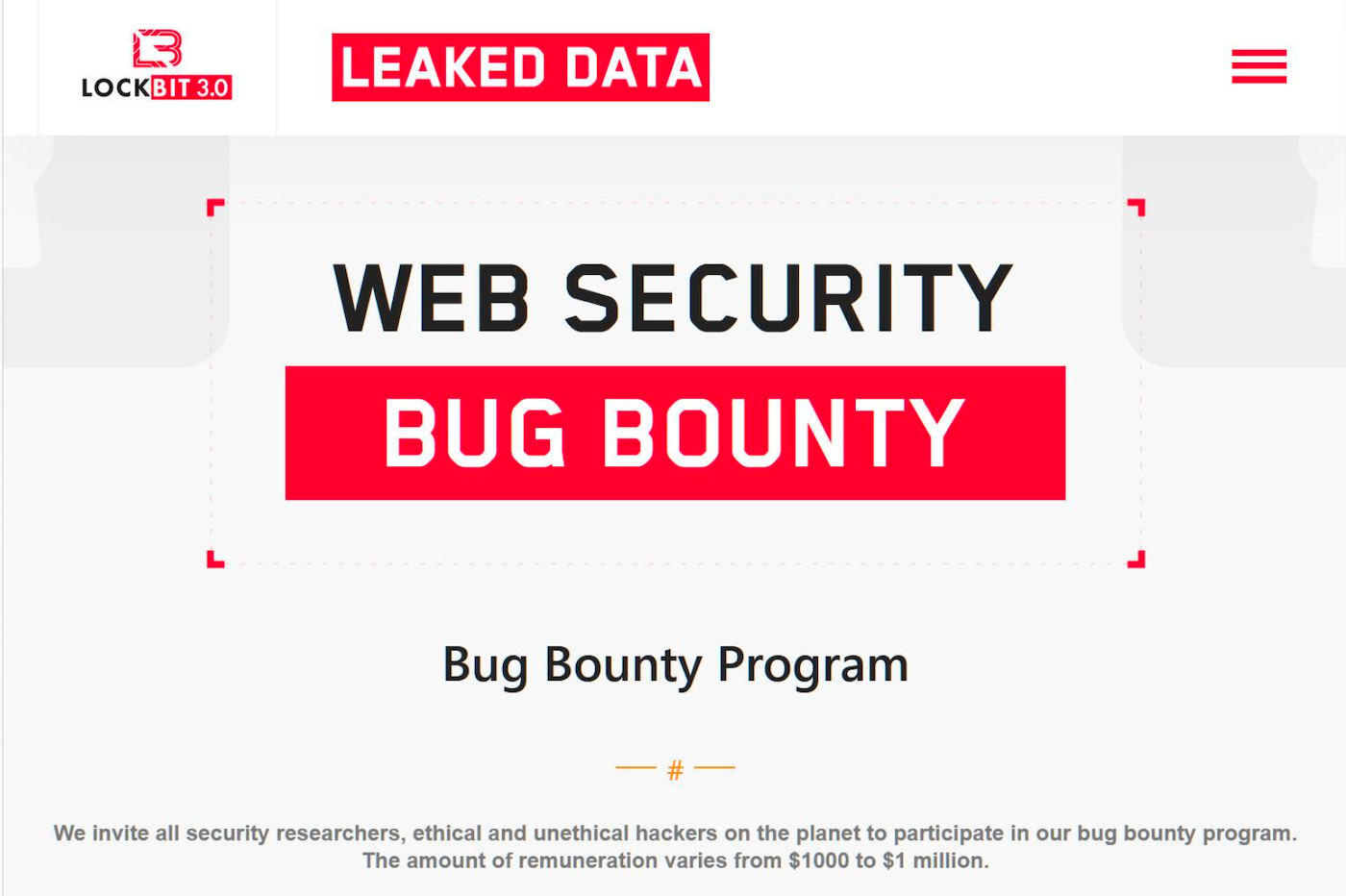
- LockBit seeks moral and unethical hackers. Supply: Akamai by way of Bleeping Laptop.
On its website, LockBit seeks moral AND Unethical hackers. Supply: Akamai by way of Bleeping Laptop.
Manufacturing, well being care in sizzling seat
Of all vertical industries, manufacturing noticed a 42% improve in whole victims in the course of the interval Akamai investigated. LockBit was behind 41% of general manufacturing assaults.
The well being care vertical noticed a 39% improve in victims throughout the identical interval, and was focused primarily by the ALPHV (also referred to as BlackCat) and LockBit ransomware teams.
SEE: Akamai focused on fake sites in analysis launched at RSA
Mitigation is greatest protection
Akamai’s suggestions on lessening the prospect of assault and mitigating the results of an incursion embrace adopting a multilayered method to cybersecurity that features:
- Community mapping to determine and isolate essential techniques and restrict community entry out and in to place fences up within the face of risk actors’ efforts at lateral motion.
- Patch, patch, patch: replace software program, firmware and working techniques.
- Story snapshots: keep common offline backups of essential knowledge and set up an efficient catastrophe restoration plan.
- Develop and recurrently check an incident response plan that outlines the steps to be taken in case of a ransomware assault. This plan ought to embrace clear communications channels, roles and obligations and a course of for participating regulation enforcement and cybersecurity consultants.
- Prepare, and practice once more: Don’t give staff, distributors and suppliers entry to organizational websites or techniques till they’ve had (common) cybersecurity consciousness coaching on phishing assaults, social engineering and different ransomware vectors.
- When you see one thing, say one thing: Encourage staff and stakeholders to report suspicious actions.
Protection is greatest offense
Protection ways, in response to Akamai, ought to embrace:
Blocking exfiltration domains
Restrict entry to providers that may be abused for knowledge exfiltration by both utilizing options that block recognized malicious url and DNS visitors, or by utilizing options or controls that permit blocking entry to particular domains.
Dangle these honey-coated fly strips
Honeypots: use them. Akamai stated they may also help lure probing attackers, luring them into servers the place their actions may be monitored
Scan and scan once more
Use an intrusion detection system to do suspicious community scans. Akamai famous that attackers use identifiable instruments to finger targets inside a company’s community. You possibly can detect them.
Test passports on the gate
Akamai suggests utilizing instruments for inspection of outgoing web visitors to dam recognized malware C2 servers. “Solutions must be able to monitor your entire DNS communications in real time and block communications to malicious domains, preventing the malware from running properly and accomplishing its goals,” the agency stated.
