Products You May Like
Get technical particulars about how this new assault marketing campaign is delivered by way of Microsoft Groups and how one can defend your organization from this loader malware.

A brand new report from international cybersecurity firm Truesec reveals a new attack campaign leveraging Microsoft Teams to infect companies’ users. Whereas the motivation of the attacker stays unknown, this DarkGate loader malware might permit its perpetrator to go for monetary acquire or cyberespionage.
Soar to:
What’s the DarkGate malware?
DarkGate is a loader malware written in Delphi; the purpose is to allow the obtain and execution of different malware as soon as it runs on an contaminated laptop. The extra malware is downloaded instantly within the reminiscence on 32- and 64-bits architectures, which makes it more durable to detect as a result of it doesn’t reside on the file system.
Different mechanisms applied within the malware makes it harder to investigate:
- Anti-VM: The malware assessments for recognized {hardware}/identifiers utilized in digital machines.
- Anti-Sandboxes: The malware checks for recognized identifiers utilized by sandbox software program.
- Anti-AntiVirus: A number of antivirus merchandise are being regarded for.
- Anti-debug: The malware typically checks for a debugger connected to the method.
- Disk house and reminiscence checks: The malware will be set to solely run with a minimal disk/reminiscence measurement.
Relying on the outcomes of all these checks, the malware would possibly alter its habits and presumably cease operating.
DarkGate has persistence capabilities that may be enabled in its configuration. In that case, it shops a replica of itself on the onerous drive and creates a registry key to be executed at reboot instances.
Though DarkGate is usually a loader for third-parties’ malware, it nonetheless has built-in capabilities.
- Info gathering: DarkGate is ready to question the system to get details about the presently logged-in person, operating software program, processes and extra, which it sends to the C2 server. It will possibly additionally gather information from the system and ship it to the C2 server, in addition to do display captures.
- Credentials theft: DarkGate is ready to steal passwords and cookies from browsers, electronic mail software program and different software program comparable to Discord or FileZilla. To attain that purpose, the malware makes use of a number of official free instruments from the favored NirSoft web site.
- Cryptomining capabilities: DarkGate is ready to begin, cease and configure a cryptominer.
- Distant entry software capabilities: DarkGate can provoke a digital community connection and execute instructions.
How new assault spreads DarkGate loader by way of Microsoft Groups
The assault consists of messages despatched on Microsoft Groups by a menace actor who used two compromised Groups accounts on the market on the Darkish Net. These accounts had been used to ship socially engineered content material to persuade customers to obtain and open a malicious archive file (Determine A).
Determine A
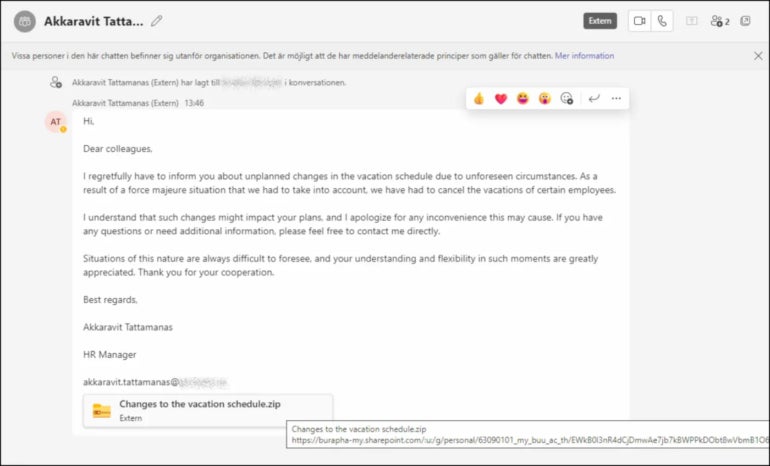
As soon as the zip file is opened, it reveals the person a malicious LNK (shortcut) file posing as a PDF doc (Determine B).
Determine B
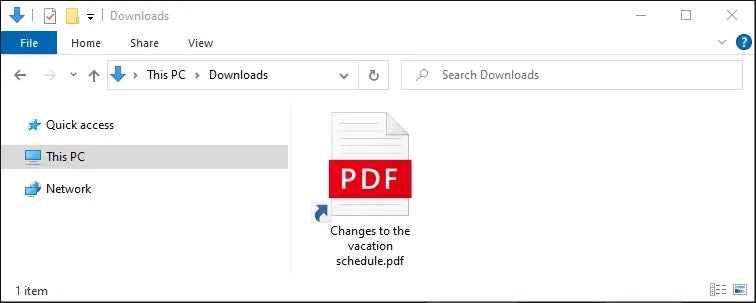
After the LNK file is clicked, it executes a command line that triggers the obtain and execution of AutoIT by way of a VBScript file. A precompiled AutoIT script can be downloaded and executed by way of the AutoIT software program.
On this assault marketing campaign, the AutoIT script checks for the presence of the Sophos antivirus; different campaigns would possibly verify for different antivirus options. If the antivirus isn’t put in, the script downloads a shellcode that in flip downloads a file, byte by byte, utilizing the stacked strings approach in an effort to remain undetected. That last payload is the DarkGate loader malware.
DarkGate’s enterprise mannequin
DarkGate loader was marketed in June 2023 by its developer RastaFarEye (Determine C), as proven in a report from German company Telekom Security.
Determine C
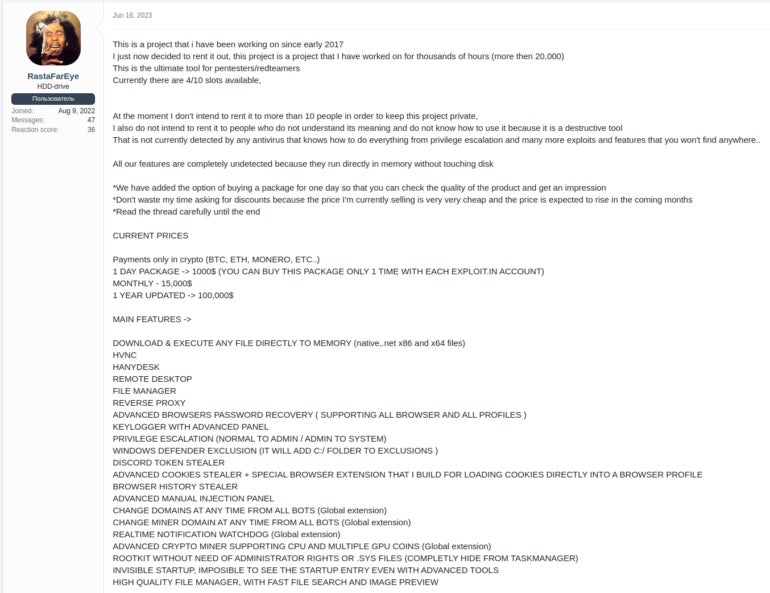
The menace actor restricted the malware-as-a-service to solely 10 associates at a month-to-month worth of $15,000 USD, or $100,000 USD for a full 12 months.
RastaFarEye additionally supplied a video displaying the malware builder and management panel (Determine D).
Determine D
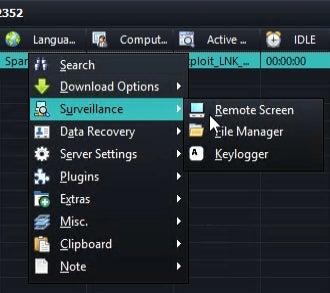
DarkGate’s capabilities makes it a software of alternative for cybercriminals occupied with monetary fraud or menace actors occupied with operating cyberespionage campaigns.
Along with creating DarkGate loader, RastaFarEye marketed more malware developed by himself, together with on Mac working techniques. The cybercriminal additionally provided Prolonged Validation certificates creation providers.
The best way to defend from DarkGate malware menace
On this assault marketing campaign, the menace actor despatched messages by way of Microsoft Groups to organizations utilizing it. So, it’s strongly suggested to not permit Microsoft Groups chat requests from exterior domains that don’t belong to the group; solely whitelisted exterior domains needs to be allowed to ship chat requests.
Other attack campaigns that delivered DarkGate loader used emails to attempt to social engineer the goal into opening a malicious file, so it’s additionally suggested to deploy safety options that analyze the URLs contained in emails along with connected information.
All working techniques and software program needs to be updated and patched to stop being compromised by frequent vulnerabilities.
Multifactor authentication needs to be deployed wherever potential, in order that even a menace actor in possession of legitimate credentials nonetheless can not entry the company atmosphere.
